Google Spyware: Difference between revisions
m (New page: When setting up performance tests, I often change my browser to use the JMeter proxy. This works well, but sometime shows up other programs sneakily running on my computer. For example i...) |
mNo edit summary |
||
| (2 intermediate revisions by the same user not shown) | |||
| Line 22: | Line 22: | ||
[[Image:googleupdate.PNG]] | [[Image:googleupdate.PNG]] | ||
Google describes [http://www.google.com/support/chrome/bin/answer.py?answer=107253&topic=14660 GoogleUpdate.exe] and states 'If you remove the GoogleUpdate process separately on your computer, you may find that your Google programs no longer function properly and, in many cases, you may see GoogleUpdate return automatically.' I'm not a big fan of programs which automatically reappear. | |||
The page describes what is in the post header, but doesn't describe what's in the URL. The URL text isn't quite base64 encoded, nor is it URL encoded. | |||
Looks like GoogleUpdate.exe is a .Net application, and is linking to these dll's | |||
<pre> | |||
$ strings GoogleUpdate.exe | |||
ADVAPI32.dll | |||
CRYPT32.dll | |||
SHELL32.dll | |||
SHLWAPI.dll | |||
USER32.dll | |||
WINTRUST.dll | |||
</pre> | |||
I'm guessing Google is encrypting some bit of data, and then sending that along with the request. It may just be enough to authenticate the request is valid, but potentially it could be other information. It should be trivial to write a proxy which intercepts all calls to CRYPT32.dll, and log it. This usually displays the information before it's encrypted. | |||
Microsoft supports signed assemblies, but the underlying C dll's are not signed. It would be fairly easy to create a proxy dll for CRYPT32.dll, and see the unencrypted data. Alternatively, I might be able to run GoogleUpdate.exe under customized version of Wine. Wine emulates the [http://wiki.winehq.org/Crypt32 Crypt32] api, so logging could be added with just a few lines of code. I'll have to save this for another day. | |||
A further look shows the updater is using these crypto APIs. | |||
<pre> | |||
$ strings GoogleUpdate.exe | grep -E "(Crypt|Cert)" | |||
CertNameToStrW | |||
CertFreeCertificateContext | |||
CertCloseStore | |||
CryptQueryObject | |||
CertDuplicateCertificateContext | |||
CertEnumCertificatesInStore | |||
</pre> | |||
It's likely using [http://msdn.microsoft.com/en-us/library/aa380264(VS.85).aspx CryptQueryObject] to verify if either itself, or an application it is reporting on is properly signed. Or maybe this is just something .Net does automatically for an app. You can see the app depends on a signed assembly. | |||
<pre> | |||
<?xml version="1.0" encoding="utf-8"?> | |||
<assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0"> | |||
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v2"> | |||
<security> | |||
<requestedPrivileges> | |||
<requestedExecutionLevel level="asInvoker" /> | |||
</requestedPrivileges> | |||
</security> | |||
</trustInfo> | |||
<dependency> | |||
<dependentAssembly> | |||
<assemblyIdentity | |||
type="win32" | |||
name="Microsoft.Windows.Common-Controls" | |||
version="6.0.0.0" | |||
processorArchitecture="X86" | |||
publicKeyToken="6595b64144ccf1df" | |||
language="*" | |||
/> | |||
</dependentAssembly> | |||
</dependency> | |||
</assembly> | |||
</pre> | |||
---- | |||
The data being posted in the URL is clearly base64 encoded. | |||
<geshi lang="bash"> | |||
printf "nwO0JIHgksk9mB9od6CikNKO8CrWf6P7E-_kUf-I6tucUaTHxi3nns4dMb11JF1N5NbyEStYRpYbNZ-0jt72d6pFUeHdWcDYq9hbVuRN8gwhdpeGLfWnyR6m8ltHlcpduojULZvw87NpboTFQ7uZCd-xHpt8BIf_veBA29qT9hssoBmPn0VcMSN7iy9iTrsg6DIEJO202bm9KHYRNkX4b9JdHmouUqxWA-QaFeN7FoxRYyV2Am3y4zZajCcSPnP5UiZ0wPYdAZ7IcY3S9tzjvDJLapzRJpdsE8EWxWakbTiKEuXKwB6TwQ4grU7TrcJJOSymFJ4TlhdOYCeqgzzh6c" | sed -re 's/(.)/\1\n/g' | sort | uniq -c | wc -l | |||
64 | |||
</geshi> | |||
Unfortunately, the decode isn't quite your standard [http://en.wikipedia.org/wiki/Base64#URL_applications URL base64 encoding]. I suspect the leading '3' indicates some kind of rot3 operation to perform first. | |||
[[Windows]] | |||
[[Security]] | |||
Latest revision as of 23:47, 29 March 2009
When setting up performance tests, I often change my browser to use the JMeter proxy. This works well, but sometime shows up other programs sneakily running on my computer. For example is shows Google traffic and del.icio.us pings.
Today, I noticed a number of annoying pings from Google.
POST /service/update2?w=3:nwO0JIHgksk9mB9od6CikNKO8CrWf6P7E-_kUf-I6tucUaTHxi3nns4dMb11JF1N5NbyEStYRpYbNZ-0jt72d6pFUeHdWcDYq9hbVuRN8gwhdpeGLfWnyR6m8ltHlcpduojULZvw87NpboTFQ7uZCd-xHpt8BIf_veBA29qT9hs
<?xml version="1.0" encoding="UTF-8"?><o:gupdate xmlns:o="http://www.google.com/update2/request" protocol="2.0" version="1.2.141.5" ismachine="0" machineid="{939A9C17-0667-4511-B5D9-75DB7840478C}" userid="{5A15CFAC-619C-4B40-A454-C537B8280AC9}" requestid="{CB9CE64C-E2C6-4FC0-B2BC-A62F9876B73A}"><o:os platform="win" version="5.1" sp="Service Pack 2"/><o:app appid="{430FD4D0-B729-4F61-AA34-91526481799D}" version="1.2.141.5" lang="" brand="GGLS" client=""><o:updatecheck/></o:app><o:app appid="{8A69D345-D564-463C-AFF1-A69D9E530F96}" version="1.0.154.48" lang="en" brand="GGLS" client=""><o:updatecheck/><o:ping active="1"/></o:app></o:gupdate>
Once upon a time I was running the Google Desktop search, and Google toolbar, but these days I'm not running any Google tools that I'm aware of.
McAfee Site Advisor reports the program might be Google's Lively. http://www.siteadvisor.com/sites/google.com/downloads/17659284/
Unfortunately, I don't see that program installed. Looks like Google decided to install 'GoogleUpdate' when I installed Google Chrome. I wouldn't mind if Chrome checked for an update when I launched it, but having it constantly check for updates when it's not running it quite bothersome.
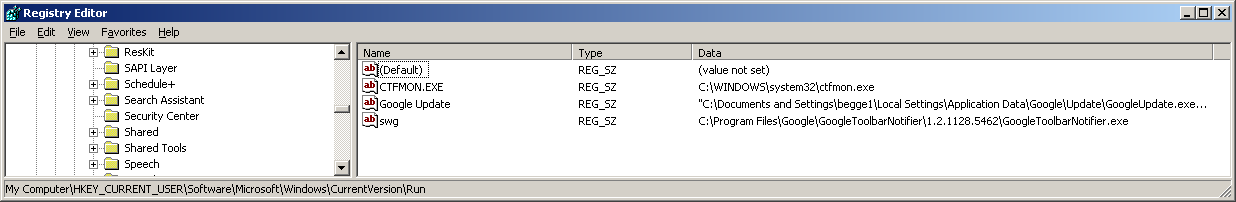
GoogleUpdate installed itself in C:\Documents and Settings\$USER$\Local Settings\Application Data\Google\Update\GoogleUpdate.exe
This blog indicated the tool came with an option to disable itself. Unfortunately, I couldn't get this to work.
So I decided I'll just delete the program, and also delete it from my registry. Turns out that the Google Toolbar doesn't uninstall it's update check. I'll be deleting that as well.
Google describes GoogleUpdate.exe and states 'If you remove the GoogleUpdate process separately on your computer, you may find that your Google programs no longer function properly and, in many cases, you may see GoogleUpdate return automatically.' I'm not a big fan of programs which automatically reappear.
The page describes what is in the post header, but doesn't describe what's in the URL. The URL text isn't quite base64 encoded, nor is it URL encoded.
Looks like GoogleUpdate.exe is a .Net application, and is linking to these dll's
$ strings GoogleUpdate.exe ADVAPI32.dll CRYPT32.dll SHELL32.dll SHLWAPI.dll USER32.dll WINTRUST.dll
I'm guessing Google is encrypting some bit of data, and then sending that along with the request. It may just be enough to authenticate the request is valid, but potentially it could be other information. It should be trivial to write a proxy which intercepts all calls to CRYPT32.dll, and log it. This usually displays the information before it's encrypted.
Microsoft supports signed assemblies, but the underlying C dll's are not signed. It would be fairly easy to create a proxy dll for CRYPT32.dll, and see the unencrypted data. Alternatively, I might be able to run GoogleUpdate.exe under customized version of Wine. Wine emulates the Crypt32 api, so logging could be added with just a few lines of code. I'll have to save this for another day.
A further look shows the updater is using these crypto APIs.
$ strings GoogleUpdate.exe | grep -E "(Crypt|Cert)" CertNameToStrW CertFreeCertificateContext CertCloseStore CryptQueryObject CertDuplicateCertificateContext CertEnumCertificatesInStore
It's likely using CryptQueryObject to verify if either itself, or an application it is reporting on is properly signed. Or maybe this is just something .Net does automatically for an app. You can see the app depends on a signed assembly.
<?xml version="1.0" encoding="utf-8"?>
<assembly xmlns="urn:schemas-microsoft-com:asm.v1" manifestVersion="1.0">
<trustInfo xmlns="urn:schemas-microsoft-com:asm.v2">
<security>
<requestedPrivileges>
<requestedExecutionLevel level="asInvoker" />
</requestedPrivileges>
</security>
</trustInfo>
<dependency>
<dependentAssembly>
<assemblyIdentity
type="win32"
name="Microsoft.Windows.Common-Controls"
version="6.0.0.0"
processorArchitecture="X86"
publicKeyToken="6595b64144ccf1df"
language="*"
/>
</dependentAssembly>
</dependency>
</assembly>
The data being posted in the URL is clearly base64 encoded. <geshi lang="bash"> printf "nwO0JIHgksk9mB9od6CikNKO8CrWf6P7E-_kUf-I6tucUaTHxi3nns4dMb11JF1N5NbyEStYRpYbNZ-0jt72d6pFUeHdWcDYq9hbVuRN8gwhdpeGLfWnyR6m8ltHlcpduojULZvw87NpboTFQ7uZCd-xHpt8BIf_veBA29qT9hssoBmPn0VcMSN7iy9iTrsg6DIEJO202bm9KHYRNkX4b9JdHmouUqxWA-QaFeN7FoxRYyV2Am3y4zZajCcSPnP5UiZ0wPYdAZ7IcY3S9tzjvDJLapzRJpdsE8EWxWakbTiKEuXKwB6TwQ4grU7TrcJJOSymFJ4TlhdOYCeqgzzh6c" | sed -re 's/(.)/\1\n/g' | sort | uniq -c | wc -l 64 </geshi>
Unfortunately, the decode isn't quite your standard URL base64 encoding. I suspect the leading '3' indicates some kind of rot3 operation to perform first.